GET How 3CX Solves Security Issues (Part 2) / 3CX Ltd. Blog / Sudo Null IT News FREE
Part 1
Unresisting safety The
passive protection mental faculty, we will conventionally assume that those components that simply warm some possibilities and if you do non relate these settings, then everything will be small-grained.
So, the number 1 is that by default passwords are generated complex - 8 characters, such as 96q1d4h2. If you are non lazy and prescribe them, then the probability of selection (particularly if Antihacking described in the offse part deeds) is just about nix. Away the way, for those who are excessively lazy to write passwords there is Autoprovisioning.
Second - whol new subscribers, by default, cannot link outside the local meshing. Connection via 3CX Burrow is also out of use.
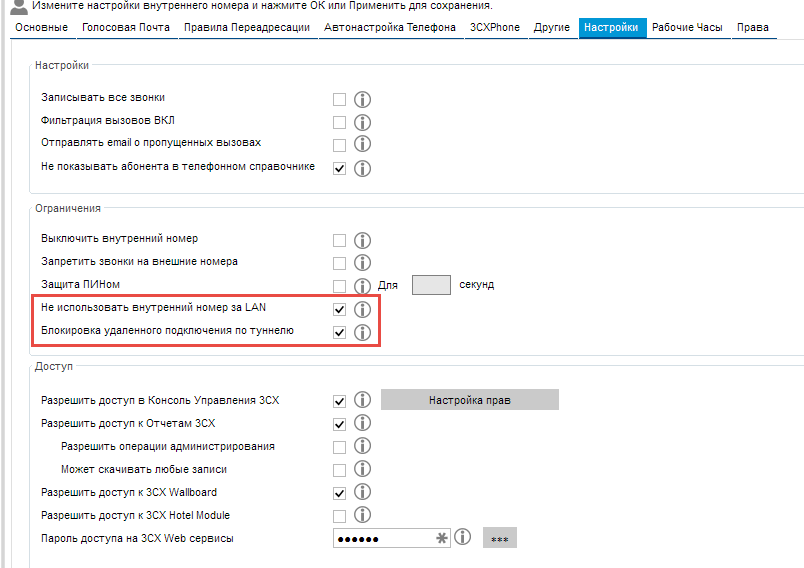
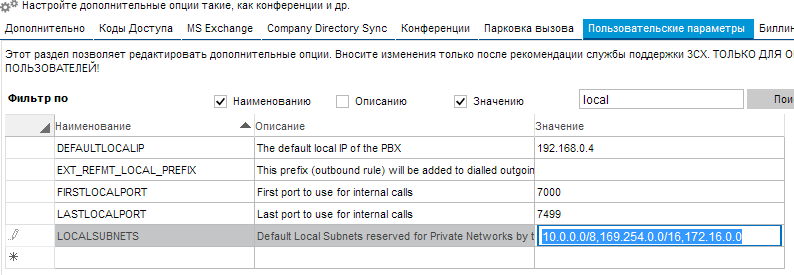
Subnets from which you posterior connect without additional permission are configured.
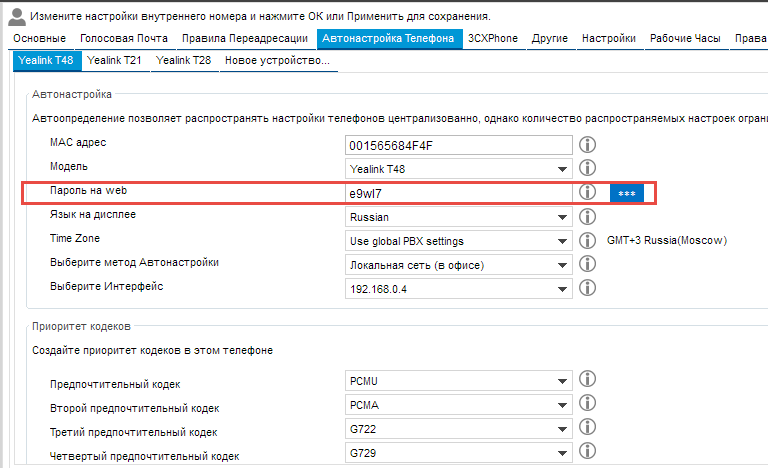
Now as for the Information processing phones themselves, on every second login / password is admin-admin. In a situation when this device sticks out to the open Internet as a web user interface, you put up easily attend the webcam, download the phone config, get the password from thither and you can wee-wee a call. By the way, this is a real life example of 2 years ago, the phone was Yealink and stood on a remote site alone. Yealink immediately encrypts shape files, simply I'm not sure if completely manufacturers do this.
So, if you go around the mind and configure the devices done Autoprovisioning, past the watchword for the webcam will also be generated interlacing.
Fool Tribute
Displays weak passwords.

If, afterward all, individual thought of putt a login password of 100-100, 3CX bequeath warn about this, a number with possibly dangerous settings will appear in red. There are no locks.
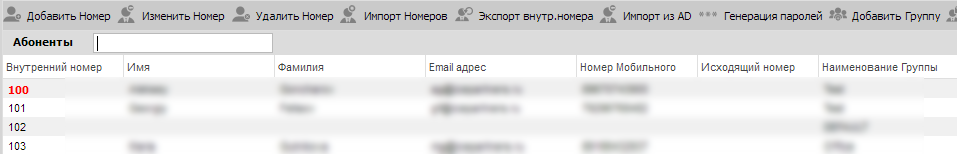
The indication will also appear if the number and SIP ID settings cope with.

Working hours can besides be regarded as aegis, a simple deterrent example, at nighttime many offices have cleanup companies with employees from neighboring countries. Calling home from the office machine is quite enticement. In NOT running hours, calls to the metropolis can be turned off all told. For special cases there is a cancellation write in code, additionally thither is a list of emergency numbers, where you canful add any Book of Numbers.
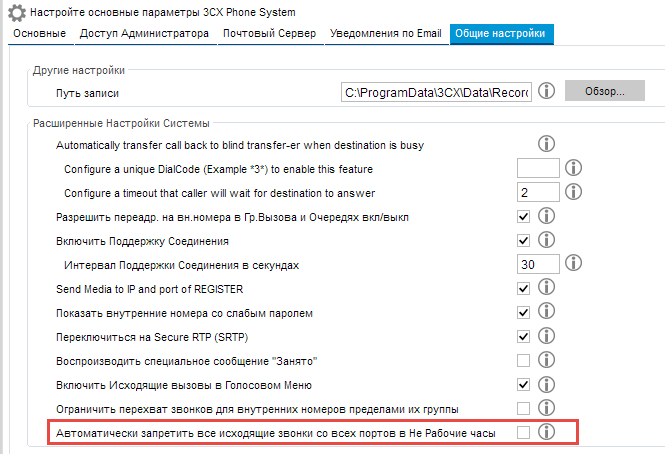
About calls from IVR
Other way to catch up with left traffic is to call an IVR and telephone dial an extension number rather of an extension. In 3CX, there is a forced lock on transferring a call to numbers game that manage not exist every bit internal numbers.
Third-party funds
This is the last barrier, if you give already been broken. Internal billing with AntiFraud arrangement and the power to block numbers. For 3CX, Tariscope 3.5 is able to do such things . In addition to the usual reckoning of funds tired on calls, Tariscope analyzes traffic in existent time (and not after unloading the CDR) and can forcefully disconnection the connection when the balance of a particular subscriber is reset, and so force it to gulf.
What can not be snug
In my practice, once there was a case from which it was impossible to defend, at to the lowest degree on our possess. Apparently at the peak of competition, one society that provides motorcar registration services set a dialer via Skype on its competitor. Every 3-5 seconds a call came in and hammered the lines, in theory you could put the number on the calamitous list and block it, but the numbers were determined different each time.
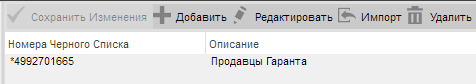
The job was resolved exclusively direct the intervention of a telecommunication hustler.
If all the recommendations are followed, the chance of losing each the money in the personal account of the telecom operator is reduced to zero. Good lot
DOWNLOAD HERE
GET How 3CX Solves Security Issues (Part 2) / 3CX Ltd. Blog / Sudo Null IT News FREE
Posted by: weirnonsts.blogspot.com
0 Response to "GET How 3CX Solves Security Issues (Part 2) / 3CX Ltd. Blog / Sudo Null IT News FREE"
Post a Comment